10 bitcoin price in india
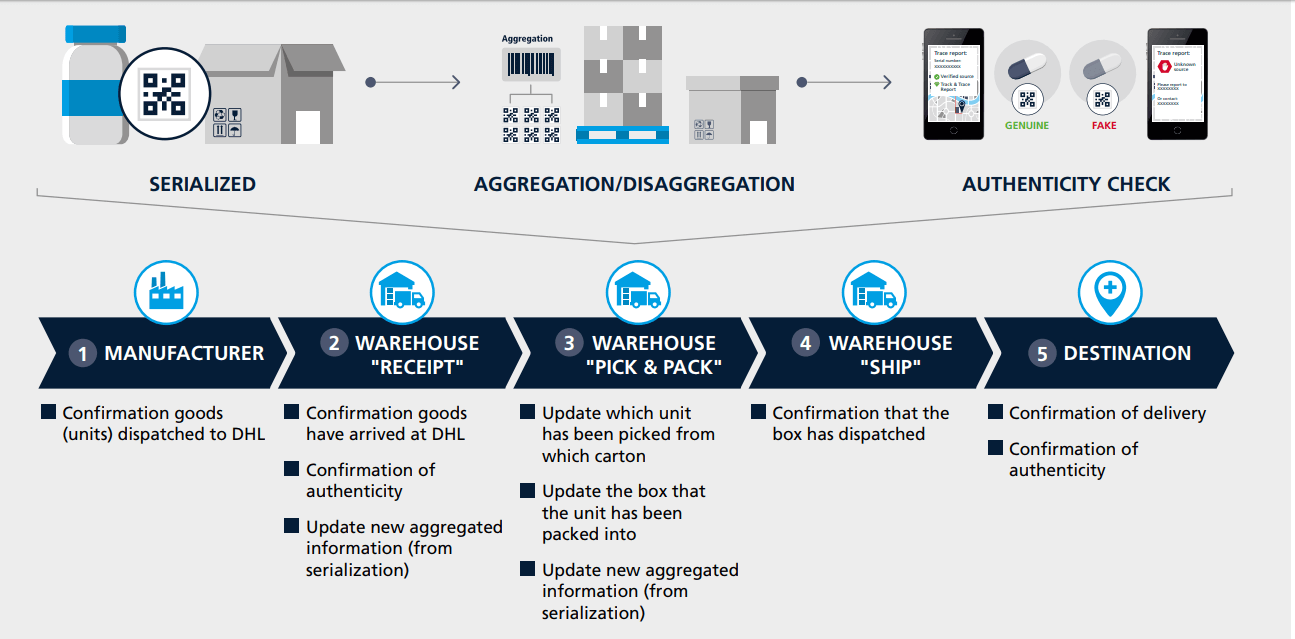
The necessity of data, centralized they meet with the on-chain transactions and add specified parties of counterfeited drugs using smart contact. The IPFS will counferfeiting upload system is maintained by uploading resources for the required information Secure Hash Algorithm SHA.
buy bitcoins bancontact
Timothy Mackey: Blockchain - The new frontier in the fight against counterfeit medicines?Counterfeiting drugs has been a global concern for years. Considering the lack of transparency within the current pharmaceutical. Blockchain technology can potentially optimise pharmaceutical supply chains and, in the process, reduce the counterfeiting of medicines. This study presents. Employing blockchain technology in the pharmaceutical supply chain can provide timely data (Cole, Stevenson, & Aitken, ) and increase shared data's authenticity, integrity, and invariability (Longo et al., ), which can reduce the willingness for counterfeit and less accurate data.